What exactly is oAuth? It’s the protocol that allows you to log in to a website using your Facebook or Google account. But how does it work? Let’s find out.
oAuth – open Authorization not open Authentication
A common misconception is that oAuth is used for authentication. It is not. It is used for authorization.
Parties involved
There are three parties involved in the oAuth process:
- Resource Owner: The user who owns the data that is being shared. (e.g. you)
- Client: The application that wants to access the data. (e.g. Facebook)
- Resource Server: The server that hosts the data.(e.g. Facebook’s server)
- Authorization Server: The server that authenticates the user and issues the access token. (e.g. Facebook’s server)
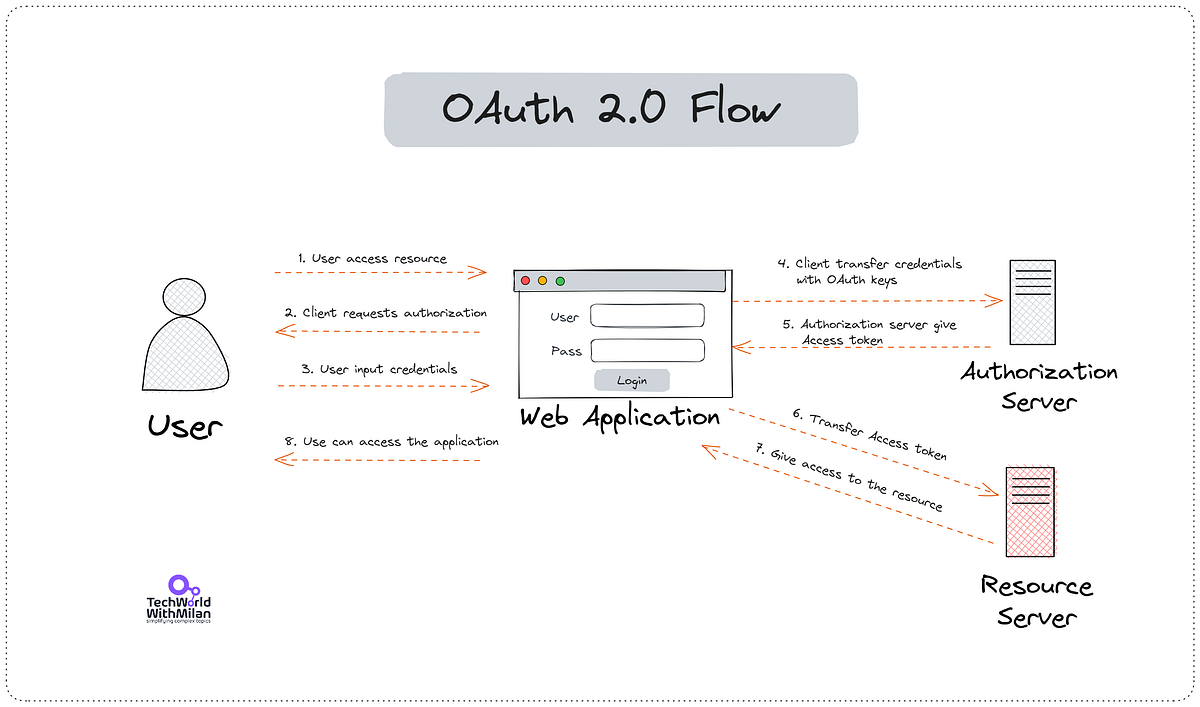
The process
Before we start, most oAuth use JWT tokens (JSON Web Tokens) for authentication. These tokens are encoded and signed, and can be verified by the server.
| Step | Description |
|---|---|
| 1 | User accesses the client application. |
| 2 | The client application redirects the user to request authorization. |
| 3 | User inputs their credentials. |
| 4 | The client application sends the user’s credentials to the authorization server with oAuth keys. |
| 5 | The authorization server authenticates the user and sends an access token to the client application. |
| 6 | The client application sends the access token to the resource server. |
| 7 | The resource server verifies the token and sends the data to the client application. |
| 8 | If the access token expires, the client application sends a refresh token to the authorization server to get a new access token. |
More about JWT
JWT tokens are encoded in three parts:
- the header,
- the payload, and
- the signature.
So it would look like:
{
header:
{
"alg": "HS256",
"typ": "JWT"
},
}
The header contains the algorithm used to encode the token, the payload contains the data, and the signature is used to verify the token.
There are two types of tokens:
- Access Token: This token is used to access the user’s data. It is short-lived and expires after a certain time.
- Refresh Token: This token is used to get a new access token when the old one expires. It is long-lived and can be used multiple times.
Why JWT is so popular?
JWT is stateless, meaning the server does not need to store the token. This makes it easier to scale and more secure.
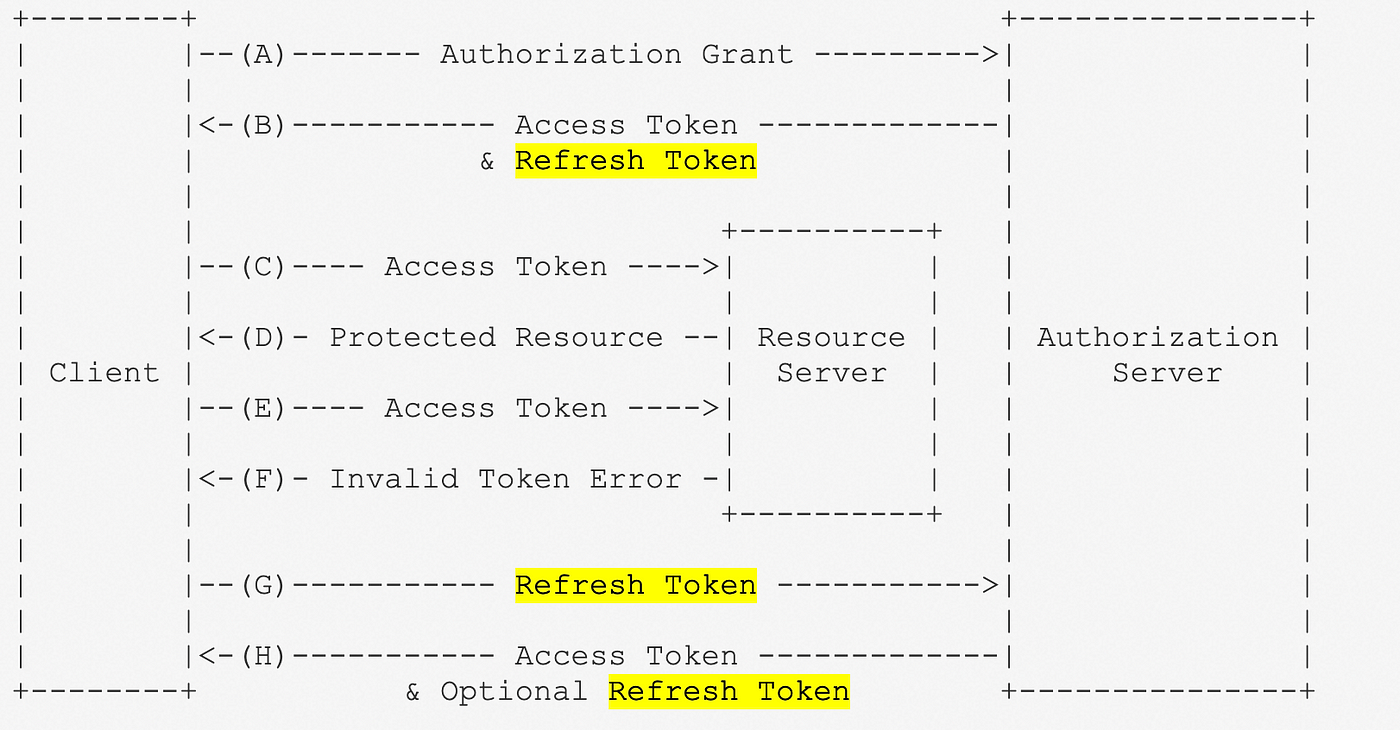
Authentication with JWT
| Step | Description |
|---|---|
| 1 | The client sends a request to the authorization server with the user’s credentials. |
| 2 | The authorization server authenticates the user and issues an access token and a refresh token. |
| 3 | The client sends the access token to the resource server. |
| 4 | The resource server verifies the token and sends the data to the client. |
| 5 | If the access token expires, the client sends the refresh token to the authorization server to get a new access token. |
| 6 | The authorization server issues a new access token and refresh token. |